HumanGov: Model Automated Multi-Tenant Architecture (MAMA) Part 3 of 3: Storing MAMA Project Configuration Files in the Cloud (AWS Codecommit) using Terraform and Git on AWSCloud9
Background
This project is about establishing cloud infrastructure for a Model Automated Multi-Tenant Architecture (MAMA), HumanGov. Each tenant (state = tenant in this case) will have their own EC2 instance, their own S3 bucket, and their own DynamoDB. (For example, Missouri and Kansas will have separate infrastructures.) The states wanted a Reusable, Multi-Tenant Software as a Service (SaaS) Application Infrastructure for dinner, and MAMA will feed it to them. This is a three part project:
HumanGov: Model Automated Multi-Tenant Architecture (MAMA), A Three-Part Series
There will not be lengthy explanations here. This post assumes that you already reviewed the ten (10)-part series on Terraform. If you want more in-depth explanation/background/information about what is going on, you can check out this 10-part series: Terraform: 10-Part Series for Familiarization
Note: If having additional background information on Git would make this easier to follow, there is a quick introductory series that you can find here: Git: 5-Part Series to Familiarize with Git
1 of 6. Open AWS Cloud9
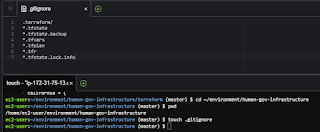
2 of 6. Create and Modify ".gitignore"
This excludes selected files from making it into the repository.
cd ~/environment/human-gov-infrastructure
pwd
touch .gitignore
".gitignore"
.terraform/
*.tfstate
*.tfstate.backup
*.tfvars
*.tfplan
*.tfr
*.tfstate.lock.info
3 of 6. Add, commit, push
git status
git add .
git status
git commit -m "AWS Infrastructure Terraform Configuration - first commit"
git push -u origin
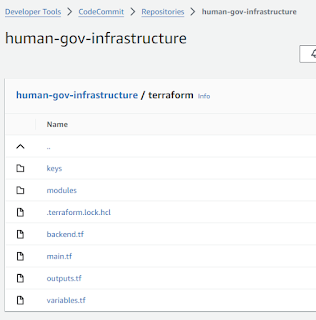
4 of 6. CodeCommit, view Terraform Files
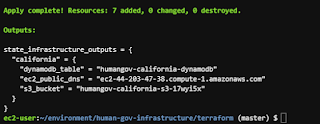
5 of 6. Spin up some resources
This is purely for evidence collection purposes in the next step.
cd ~/environment/human-gov-infrastructure/terraform
pwd
terraform apply
6 of 6. Final Documentation and Clean-Up:
Here is some evidence to support that these tasks were done within a certain AWS account.
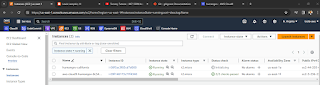
Evidence 1 of 5. EC2 Instance provisioned through Terraform
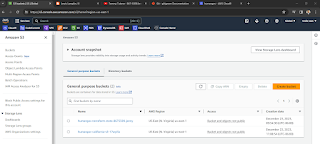
Evidence 6.2 of 5. S3 Buckets for the State File and State of California
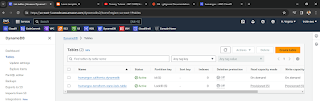
Evidence 3 of 5. DynamoDB tables for State Lock and State of California
Evidence 4 of 5. AWS CodeCommit showing the Terraform files
Evidence 5 of 5. Terraform output showing that the resources were destroyed
terraform destroy
terraform show
Reference






Comments
Post a Comment